Was this article helpful?
Thanks for your feedback
Proof Key for Code Exchange (PKCE) is a security extension for OAuth 2.0 to avoid malicious attacks and perform a secure authorization flow.
In PKCE flow, the calling application creates a secret key that the authorization server can verify, called the code verifier. The calling application converts the code verifier value into a code challenge and sends it over HTTPS to retrieve the authorization code. The entire process prevents attackers from interfering with the authorization flow, therefore enhancing its security.
PKCE makes use of a unique string code_verifier making client_secret an optional parameter.
In the authorization request, the unique string code_challenge_method is used to derive the code_challenge parameter. The code_challenge_method can be either plain or S256.
The code_challenge_method is optional. If it is not mentioned in the request, the system takes plain as the default method.
The standard authorization flow serves as the foundation for PKCE enabled authorization flows.
Some modifications for the PKCE authorization flow are as follows:
{BASE_URL}/#!/apps/{app_uid}/authorize?response_type=code&client_id={client_id}&redirect_uri={redirect_uri}&scope={scope}&state={state}&code_challenge={code_challenge}&code_challenge_method={plain/S256}Note: The parameter code_challenge_method is optional and when not included in the request, the default value plain is considered.
POST {BASE_URL}/apps-api/apps/token
Headers:
Content-Type: application/x-www-form-urlencoded
Request Body:
grant_type:authorization_code
client_id:{client_id}
redirect_uri:{redirect_uri}
code:{authorization_code}
code_verifier:{code_verifier}Note: After enabling PKCE, the client_secret parameter is optional. If you still provide the parameter for the User Token, then it should also be added for the Refresh Token.
POST {BASE_URL}/apps-api/apps/token
Headers:
Content-Type: application/x-www-form-urlencoded
Request Body:
grant_type:refresh_token
client_id:{client_id}
redirect_uri:{redirect_uri}
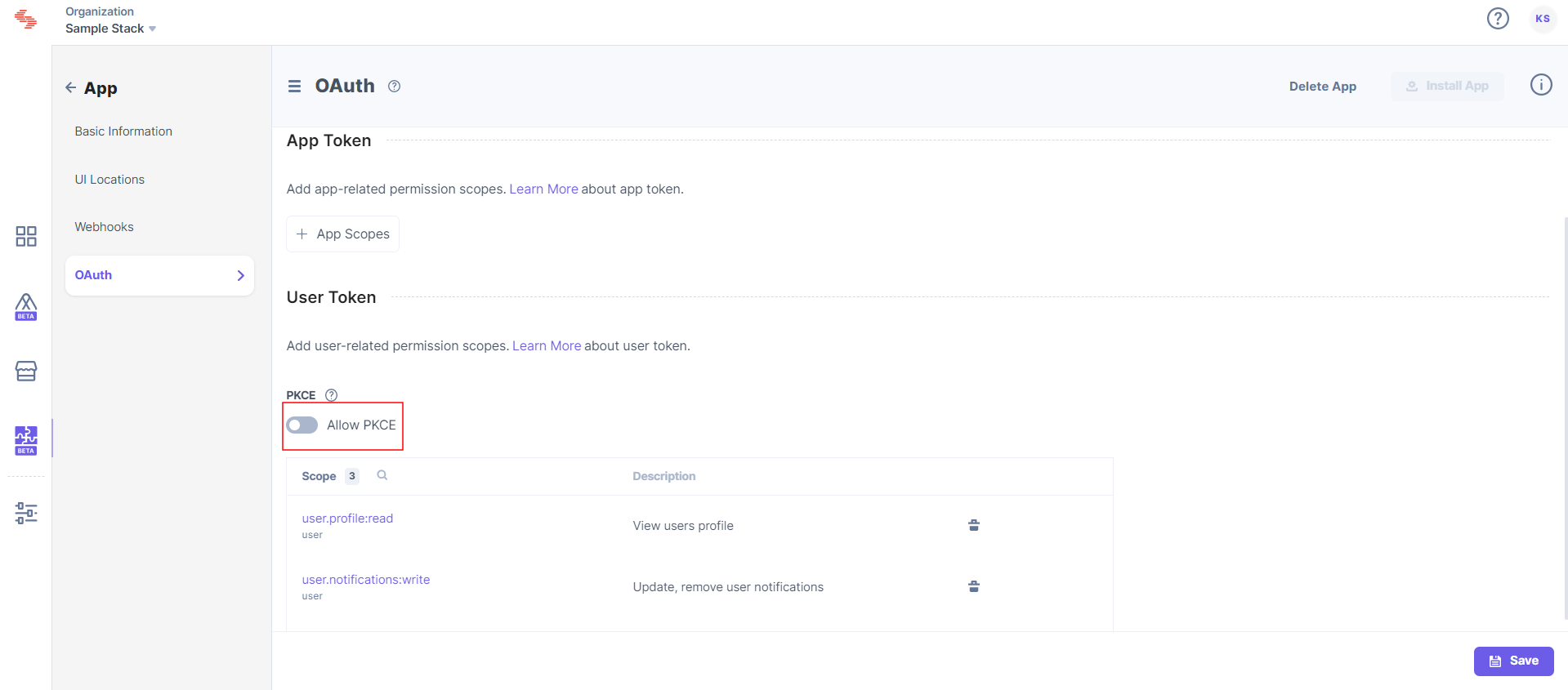
refresh_token:{refresh_token}To enable PKCE for your application, follow the steps given below:
Was this article helpful?
Thanks for your feedback