Was this article helpful?
Thanks for your feedback
Contentstack OAuth uses the OAuth 2.0 protocol that allows external applications and services to access Contentstack APIs on behalf of a user. You can implement an OAuth connection to Contentstack by creating apps in the Developer Hub console.
Contentstack OAuth allows the resource owner (user) to share the protected data from the Contentstack resource server (API) without sharing their credentials. For that matter, the Contentstack OAuth server issues access tokens (App & User tokens) that the client applications can utilize to access restricted data on behalf of the resource owner.
Some scenarios in which you can use Contentstack OAuth are as follows:
Since Contentstack is hosted at multiple data centers, the API domain URL varies for each data center. Learn more about Contentstack Regions.
Private apps only authorize specific organization members in which the app is developed. Suppose you want your application to execute OAuth capabilities across all regions/data centers. In that case, you need to publish your app either as a Public App or a Public Unlisted App.
Additional Resource: Learn more about app visibility status.
Here, the developers need to identify which data center the client has authorized the app from and the region the organization is hosted. After authorization, developers can identify the region using the location parameter in the redirected URL.
The regional parameters are as follows:
| Region | Parameter |
North American | NA |
Europe | EU |
| Azure North American | AZURE_NA |
This is required as all Contentstack API’s are scoped to the region.
There are two types of OAuth tokens that you can generate with your applications:
The App Token is associated with installed applications. The scope of an app token differs from that of a user token. Here are a few properties of the app token:
The User Token is associated with the users who authorized it. The scope of a user token differs from that of an app token. Here are a few properties of the user token:
Currently, user tokens and app tokens are valid for 60 minutes only. You can generate new tokens by following the Refresh Token flow.
You can create custom applications in Developer Hub. It provides the necessary tools to develop an app. While developing apps, you can integrate your application with the Contentstack OAuth.
To integrate your app with Contentstack OAuth, log in to your Contentstack account and follow the steps below:
Configuring OAuth and its scopes allows your app to perform tasks in your development workspace. You can configure and select scopes through the OAuth option available in your app.
To configure OAuth, log in to your Contentstack account and follow the steps below:
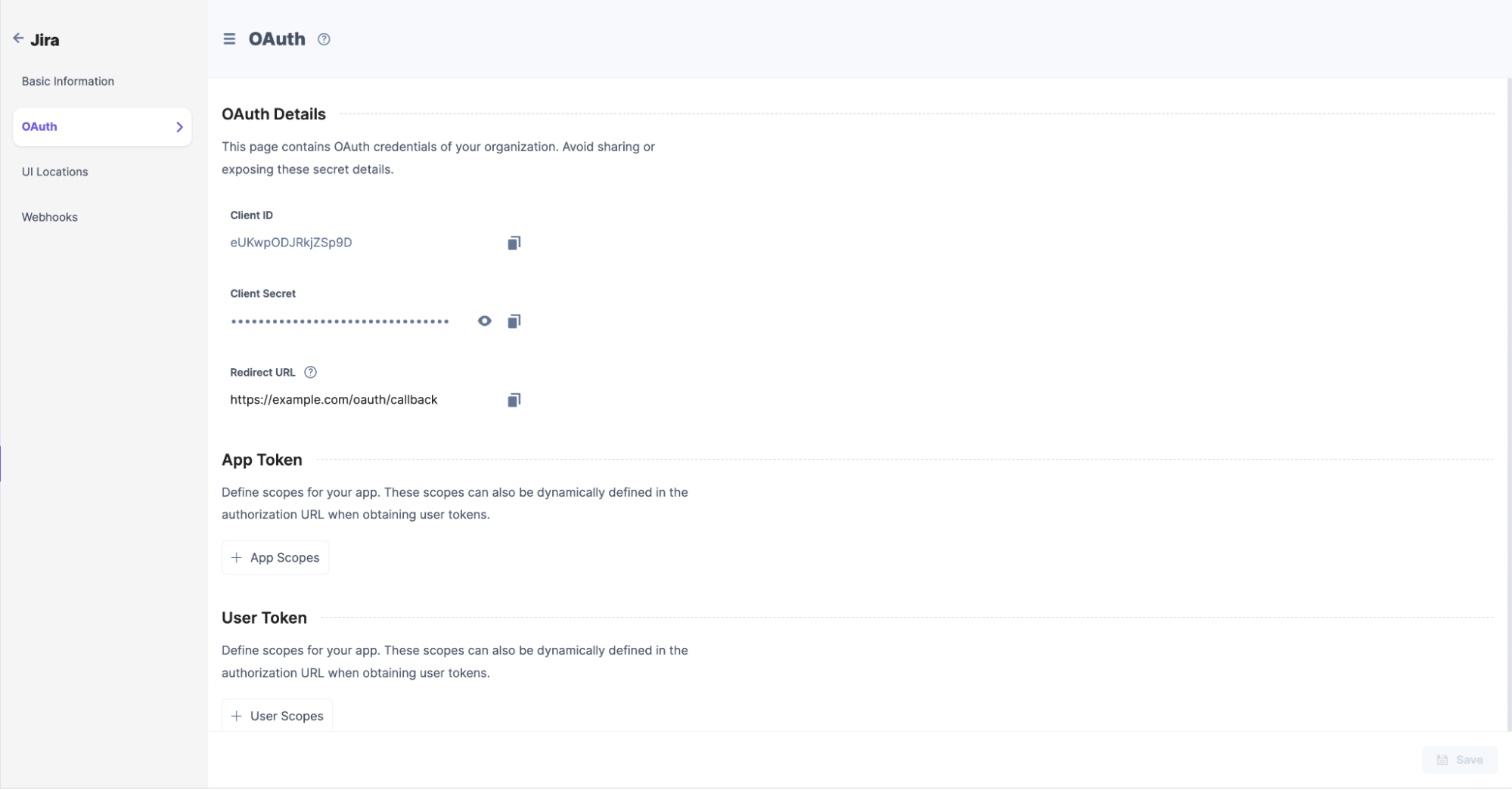
Note: User permission scopes can be passed dynamically in the Authorization URL while authorizing a user.
Next, you can check out how to add the App and User Token Scopes.
In the OAuth page, you will find the App Token section that lets you add app-related permission scopes.
To do so, perform the following steps:
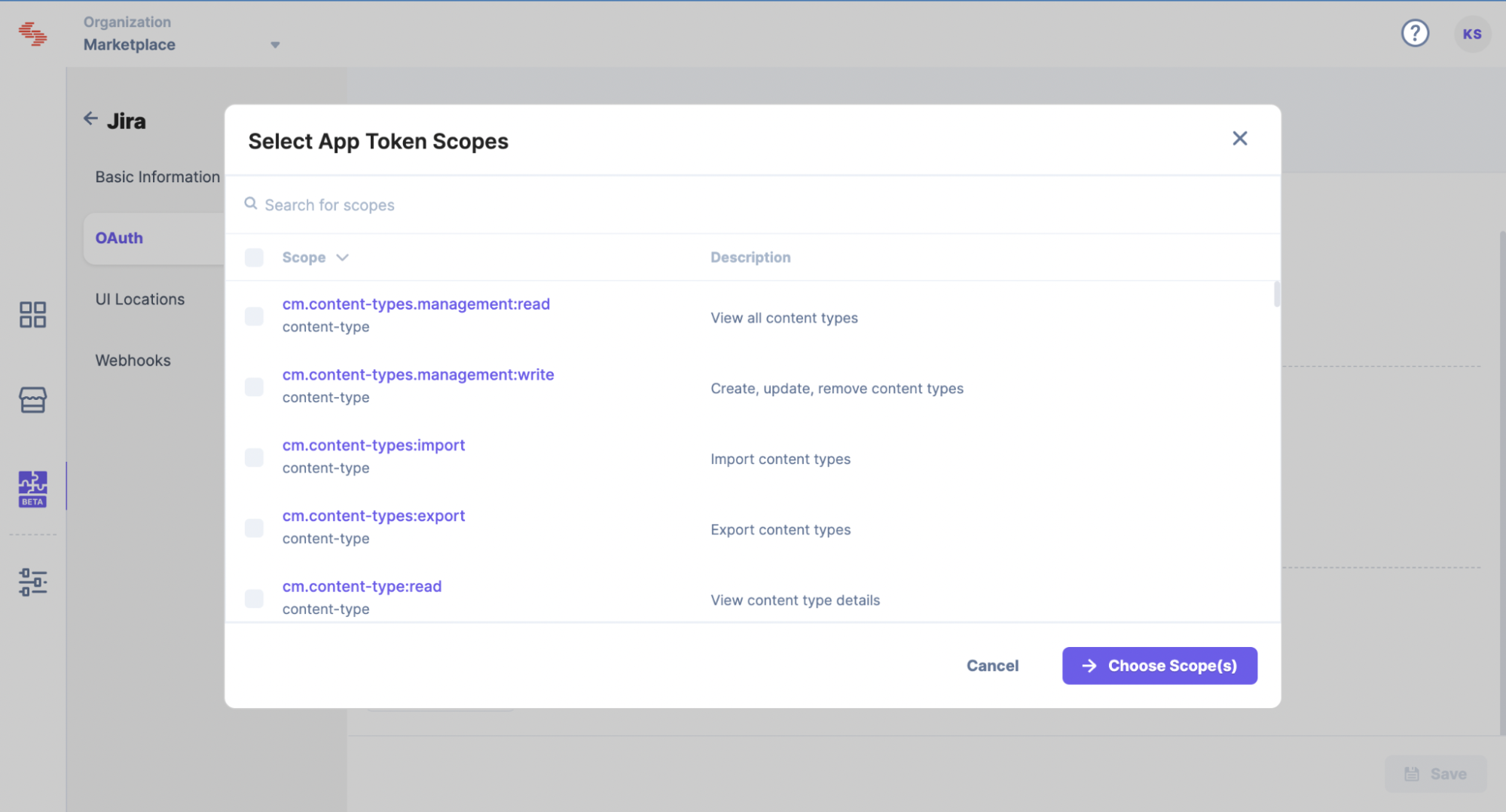
In the OAuth page, you will find the User Token section that lets you add user-related permission scopes.
To do so, perform the following steps:
Additional Resource: Learn more about the app and user token scopes from the OAuth Scopes document.
Note: You can find the App UID in the basic information section of the app. All query parameters should be URL-encoded.
App Token:
{BASE_URL}/#!/apps/{app_uid}/install
For instance, for North America (NA) region, the Authorization URL will look something like this:https://app.contentstack.com/#!/apps/627e126bbe975e0*********/install
User Token:
{BASE_URL}/#!/apps/{app_uid}/authorize?response_type=code&client_id={client_id}&redirect_uri={redirect_uri}&scope={scope}&state={state}
For instance, for North America (NA) region, the Authorization URL will look something like this:https://app.contentstack.com/#!/apps/627e126bbe975e0*********/authorize?response_type=code&client_id=428ub0q0w*******&redirect_uri=https://example.com/oauth/callback&scope=user:read
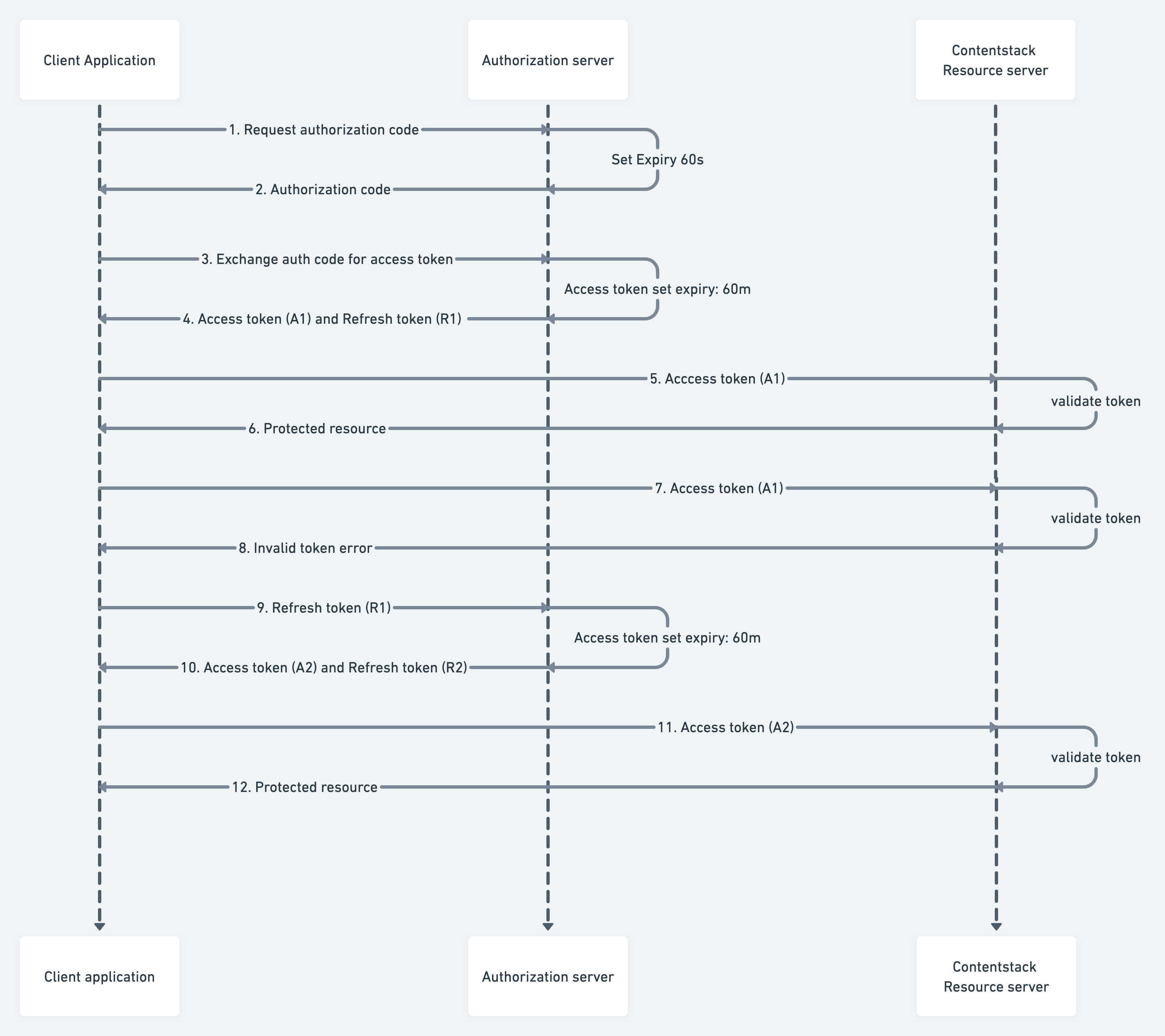
Implement the flow described below to obtain an authorization code using App and User token. Once you get the authorization code > exchange it for an access token.
https://app.contentstack.com/#!/apps/627e126bbe975e0*********/install
https://example.com/oauth/callback?code={authorization_code}&location=NANote: This code is only valid for 60 seconds.
https://app.contentstack.com/#!/apps/627e126bbe975e0*********/authorize?response_type=code&client_id=428ub0q0w*******&redirect_uri=https://example.com/oauth/callback&scope=user:read
https://example.com/oauth/callback?code={authorization_code}&location=NANote: This code is only valid for 60 seconds.
Exchange the authorization code for the access token by calling the token endpoint having the grant type of authorization_code and the parameter code containing the newly generated code from the previous step. For instance:
POST {BASE_URL}/apps-api/apps/token
Headers:
Content-Type: application/x-www-form-urlencoded
Request Body:
grant_type:authorization_code
client_id:{client_id}
client_secret:{client_secret}
redirect_uri:{redirect_uri}
code:{authorization_code}
The request in curl takes the following form:
curl --location --request POST 'https://app.contentstack.com/apps-api/apps/token' \ --header 'Content-Type: application/x-www-form-urlencoded' \ --data-urlencode 'grant_type=authorization_code' \ --data-urlencode 'client_id=your_client_id' \ --data-urlencode 'client_secret=your_client_secret' \ --data-urlencode 'redirect_uri=your_redirect_uri' \ --data-urlencode 'code=your_auth_code'
On the success of the token call, an access token is provided along with the refresh token.
The response will look something like this:
{
"access_token": "c89977e8de8bafcac88d************",
"refresh_token": "e5998ca04d0b2f72b72c************",
"token_type": "Bearer",
"expires_in": 3600,
"location": "NA",
"organization_uid": "bltbab185**********",
"authorization_type": "app",
}Note:: This token is only valid for 60 minutes.
Your access token allows you to call the methods described by the permission scopes you set during authorization. For instance:
Scope: cm.stacks.management:read
API Call:
API_BASE_URL for different regions supported by Contentstack are:
US (North America, or NA): https://api.contentstack.io
Europe (EU): https://eu-api.contentstack.com
Azure NA: https://azure-na-api.contentstack.com
You can use the endpoint as per the designated region.
GET {API_BASE_URL}/v3/stacks
Headers:
authorization: Bearer your_access_token
organization_uid: your_organization_uid
The request in curl takes the following form:
curl --location --request GET 'https://api.contentstack.io/v3/stacks' \ --header 'authorization: Bearer your_access_token' \ --header 'organization_uid: your_organization_uid'
The OAuth flow begins with a user interacting with your app and ends with your app authorized to access Contentstack resources in a way dictated by the user.
The access token allows you to access the app's data. With a regular expiration for your access token, the danger of the token falling into the wrong hands is reduced. But to maintain control over app data, your app needs a way to request a new access token regularly.
A refresh token allows your app to rotate its access tokens seamlessly, using the same token endpoint to acquire a new access token with the help of previously generated refresh token.
On the access token expiry, pass the refresh token obtained from the previous access token call in the code parameter. For instance:
POST {BASE_URL}/apps-api/apps/token
Headers:
Content-Type: application/x-www-form-urlencoded
Request Body:
grant_type:refresh_token
client_id:{client_id}
client_secret:{client_secret}
redirect_uri:{redirect_uri}
refresh_token:{refresh_token}
The request in curl takes the following form:
curl --location --request POST 'https://app.contentstack.com/apps-api/apps/token' \ --header 'Content-Type: application/x-www-form-urlencoded' \ --data-urlencode 'grant_type=refresh_token' \ --data-urlencode 'client_id=your_client_id' \ --data-urlencode 'client_secret=your_client_secret' \ --data-urlencode 'redirect_uri=your_redirect_uri' \ --data-urlencode 'refresh_token=your_refresh_token'
Was this article helpful?
Thanks for your feedback